VoIP security is a critical concern for businesses relying on internet-based communication systems. As cyber threats increase, protecting your VoIP network from potential attacks has become more important than ever.
At UCaaS Review, we’ve seen firsthand the devastating impact of security breaches on VoIP systems. This guide will equip you with essential strategies to fortify your network against common threats and maintain secure communications.
Top VoIP Security Threats You Need to Know
VoIP networks face numerous security challenges that can compromise sensitive data and disrupt business operations. This chapter explores the most prevalent threats that businesses must guard against to maintain secure communications.
Eavesdropping and Call Interception
Eavesdropping poses a significant risk to VoIP systems. Attackers intercept and listen to VoIP calls, potentially stealing confidential information (including financial data and trade secrets). To combat this threat, businesses should prioritize end-to-end encryption for all VoIP communications, configure VoIP-specific firewalls, and employ strong authentication measures.
Denial of Service (DoS) Attacks
DoS attacks cripple VoIP networks by flooding them with traffic, rendering the system unusable. These attacks often result in significant downtime and financial losses. In Q4 of 2023, DDoS attack traffic targeting Taiwan registered a 3,370% growth compared to the previous year, amidst the upcoming general election and reported tensions. To mitigate this risk, companies must implement robust firewalls and intrusion detection systems specifically configured for VoIP protocols.
Voice Phishing (Vishing)
Vishing is a form of social engineering where attackers impersonate trusted entities to extract sensitive information. This threat exploits human trust rather than technical vulnerabilities, making it particularly dangerous. Companies should educate their employees about vishing tactics and implement caller ID verification systems to reduce the risk of falling victim to these scams.
VoIP Spoofing and Toll Fraud
VoIP spoofing involves manipulating caller ID information to deceive recipients. This can lead to unauthorized access to systems or financial fraud. Toll fraud (where attackers hijack VoIP systems to make expensive international calls) can result in substantial financial losses. Implementing strict access controls and regularly monitoring call logs for unusual patterns helps detect and prevent these threats early.

To effectively protect VoIP networks, companies must adopt a multi-layered security approach. This includes technical measures like encryption and firewalls, as well as employee training and vigilant monitoring. The next chapter will explore essential VoIP security measures that businesses can implement to fortify their networks against these common threats.
How to Secure Your VoIP Network: Essential Measures
VoIP network security requires a comprehensive approach. We’ve identified key security measures that businesses should implement to safeguard their communications.
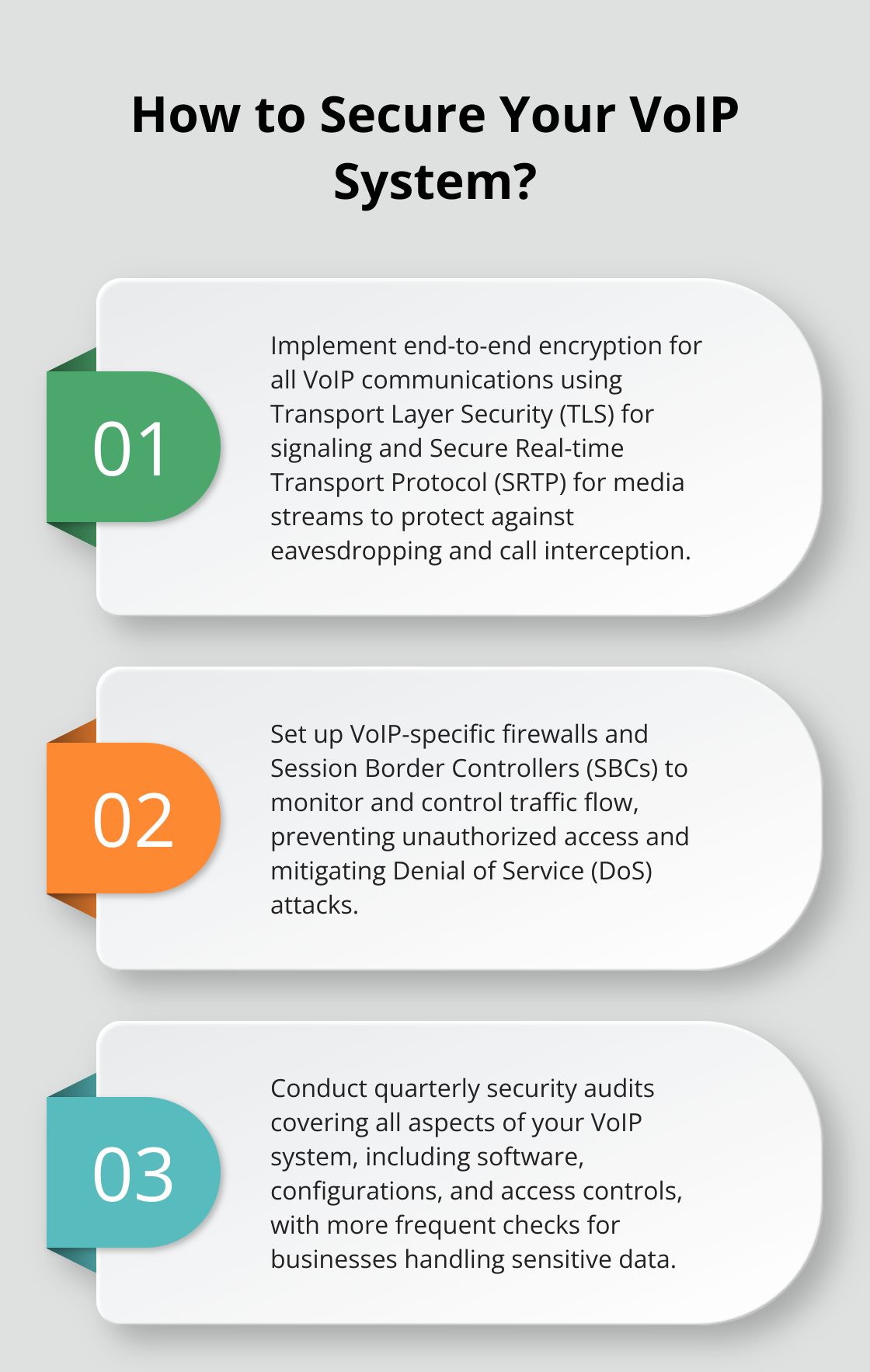
Implement Strong Encryption Protocols
Encryption protects VoIP calls from interception. Use Transport Layer Security (TLS) for signaling and Secure Real-time Transport Protocol (SRTP) for media streams. These protocols ensure that intercepted data remains indecipherable. Cisco estimates that by 2023, there will be 15.4 million distributed denial-of-service attacks (DDoS) attacks alone.
Use Virtual Private Networks (VPNs)
The rise of remote work has made Virtual Private Networks (VPNs) essential. VPNs create a secure tunnel for your VoIP traffic, protecting it from eavesdropping and man-in-the-middle attacks. Cybersecurity Ventures predicts that 60% of global enterprises will use VPNs for secure remote access by 2025.
Enable Firewalls and Session Border Controllers
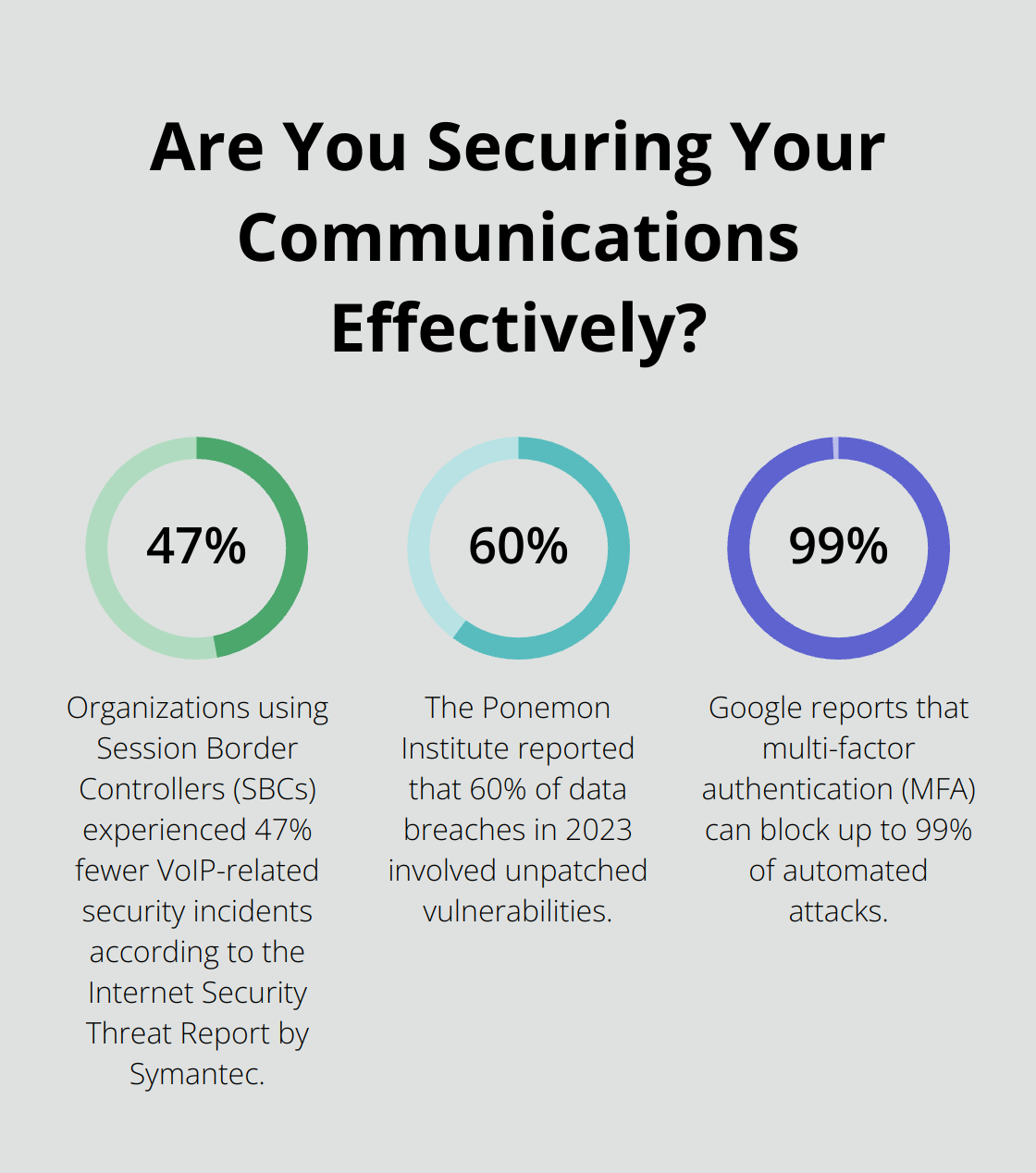
VoIP-specific firewalls and Session Border Controllers (SBCs) monitor and control the flow of your VoIP traffic. These tools prevent unauthorized access and mitigate Denial of Service (DoS) attacks. The Internet Security Threat Report by Symantec found that organizations using SBCs experienced 47% fewer VoIP-related security incidents.
Regularly Update and Patch Systems
Outdated software is a major vulnerability. Establish a rigorous update schedule for all VoIP-related systems (including phones, servers, and applications). The Ponemon Institute reported that 60% of data breaches in 2023 involved unpatched vulnerabilities.
Enforce Strong Password Policies
Weak passwords remain a significant security risk. Enforce complex password requirements, including a mix of uppercase and lowercase letters, numbers, and symbols. Implement multi-factor authentication (MFA) for an extra layer of security. Google reports that MFA can block up to 99% of automated attacks.
These measures will significantly enhance your VoIP network’s security. However, technology alone isn’t enough. The next chapter explores best practices that combine technical solutions with human vigilance to create a robust security posture for your VoIP system.
How to Strengthen Your VoIP Network Security
Conduct Regular Security Audits
Regular security audits are essential for identifying and addressing new vulnerabilities as they emerge. These audits should cover all aspects of your VoIP system, including software, configurations, and access controls. Conduct these audits at least quarterly, with more frequent checks for businesses handling sensitive data.
Empower Employees Through Security Training
Employees form the first line of defense against VoIP security threats. Implement a comprehensive security awareness training program covering VoIP-specific risks (such as vishing and social engineering attacks). Make this training mandatory for all employees and conduct refresher courses twice a year.

The Ponemon Institute found that organizations with a strong security awareness culture experience 52% fewer security incidents. Include practical exercises in your training, such as simulated phishing attempts, to help employees recognize and respond to real-world threats.
Implement Advanced Traffic Monitoring
Continuous monitoring of VoIP network traffic detects and responds to security threats in real-time. Implement an intrusion detection system (IDS) configured for VoIP protocols. One advantage of employing anomaly-based systems is that they are effective at finding zero-day and unidentified attacks, although they could produce a lot of false positives.
Strengthen Access Controls with Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra security layer to your VoIP system. Users must provide two or more verification factors to gain access, significantly reducing unauthorized access risk, even if passwords are compromised.
Google reports that MFA can block up to 99.9% of automated attacks. When implementing MFA for your VoIP system, use a combination of something the user knows (like a password), something they have (like a smartphone app), and something they are (like a fingerprint).
Isolate VoIP Traffic Through Network Segmentation
Network segmentation divides your network into smaller, isolated segments. Separating VoIP traffic from other data traffic limits potential damage if one part of your network is compromised.
The SANS Institute found that 74% of organizations implementing network segmentation reported improved network security. Use virtual LANs (VLANs) to isolate VoIP traffic and implement strict access controls between segments.
Final Thoughts
VoIP security threats pose significant risks to businesses, but effective countermeasures exist. Encryption protocols, VPNs, firewalls, and regular system updates form the foundation of a secure VoIP infrastructure. Strong password policies and multi-factor authentication create a formidable defense against potential attackers.
Employee training, security audits, and network monitoring complement technical solutions for comprehensive VoIP security. These practices ensure that your team remains vigilant and your systems stay ahead of emerging threats. VoIP security requires ongoing attention and adaptation to the changing threat landscape.
We at UCaaS Review have developed a platform that matches businesses with top UCaaS providers in minutes, considering specific security needs. Our service helps you find secure VoIP solutions tailored to your communication requirements. Prioritize VoIP security to protect your communications infrastructure and maintain client trust.



