UCaaS security is a critical concern for modern businesses relying on cloud-based communication systems. As cyber threats evolve, Chief Information Officers (CIOs) must stay ahead of potential vulnerabilities to protect sensitive data and maintain operational continuity.
At UCaaS Review, we’ve compiled essential security best practices that every CIO should know to safeguard their organization’s communication infrastructure. This guide will explore common risks, crucial security measures, and regulatory considerations to help you fortify your UCaaS environment.
Key UCaaS Security Risks Every CIO Must Address
Vulnerabilities in UCaaS Infrastructure
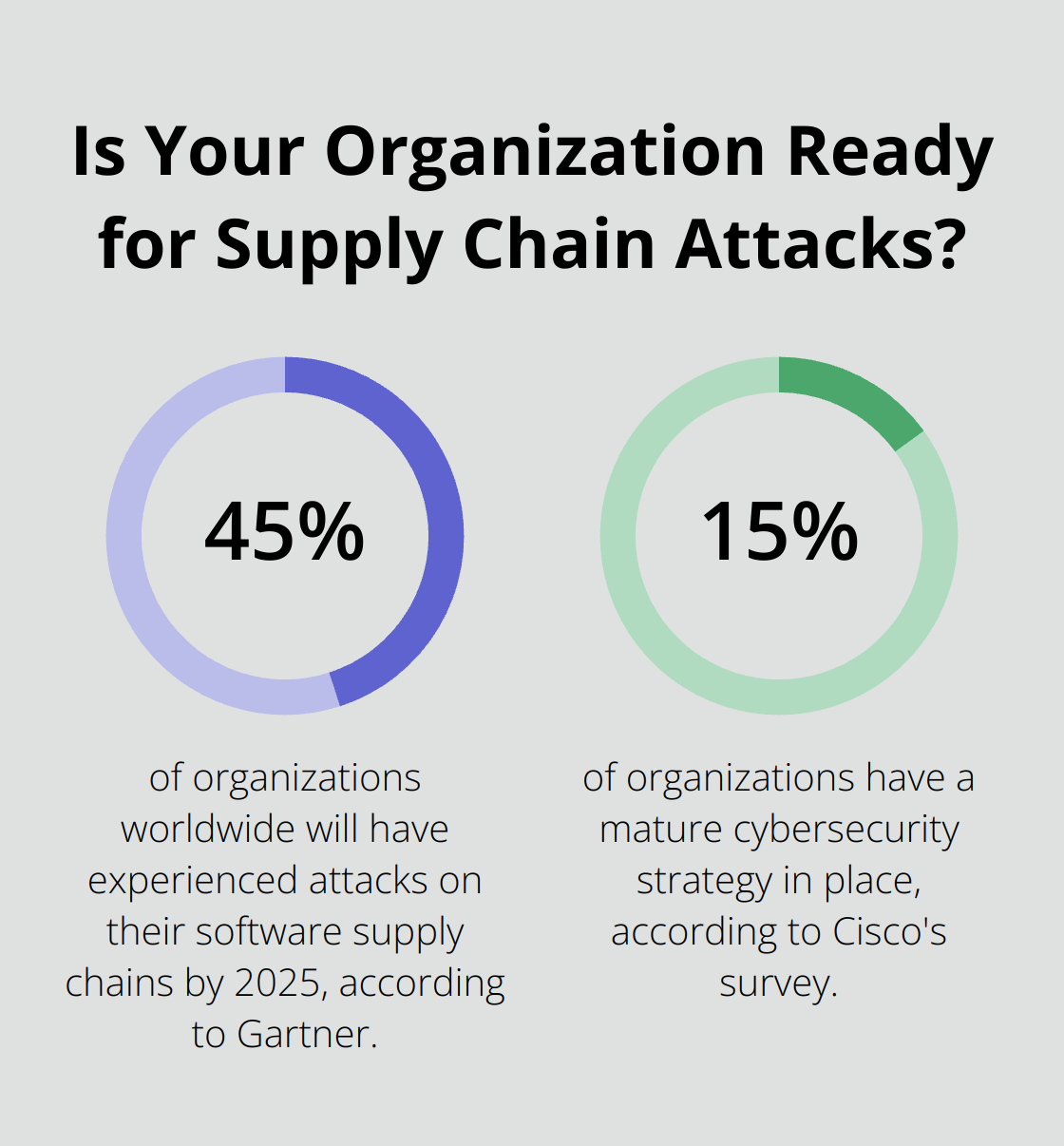
The security of Unified Communications as a Service (UCaaS) infrastructure presents significant challenges for Chief Information Officers (CIOs). Gartner predicts that by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021. This statistic underscores the critical need for proper setup and ongoing management of UCaaS systems.
Common weak points that cybercriminals exploit include misconfigured APIs, weak authentication protocols, and outdated software versions. CIOs must ensure their UCaaS providers offer robust security measures and that their IT teams possess the necessary expertise to maintain these systems effectively.
Threats to Communication Data
The sensitive nature of business communications makes UCaaS platforms attractive targets for cybercriminals. Eavesdropping, man-in-the-middle attacks, and data interception pose real threats that can compromise confidential information.
Cisco’s survey revealed that only 15% of organizations have a mature cybersecurity strategy in place. In the context of UCaaS, this could result in unauthorized access to voice calls, video conferences, or instant messages, potentially leading to data breaches or corporate espionage.
Business Impact of Security Breaches
Security breaches in UCaaS systems can have severe and far-reaching consequences. The immediate financial impact is substantial, with long-term repercussions extending beyond financial losses.
Reputational damage is a significant concern. For businesses that rely on UCaaS for customer interactions, a security incident could result in a loss of customer trust and loyalty.
Operational disruptions also pose a critical risk. A compromised or offline UCaaS system due to a security breach can paralyze communication within an organization and with external stakeholders. This downtime can lead to lost productivity and revenue.
Regulatory Compliance Challenges
The increasing focus on data protection regulations (such as GDPR and CCPA) means that security breaches in UCaaS systems can lead to significant legal and compliance issues. Fines for non-compliance can be substantial.
CIOs must remain vigilant in addressing these UCaaS security risks. Regular risk assessments, employee training, and partnerships with reputable UCaaS providers are essential steps in mitigating these threats.
As we move forward to explore essential UCaaS security measures, it becomes clear that a proactive and comprehensive approach is necessary to protect an organization’s communication infrastructure. The next section will outline specific strategies and best practices that CIOs can implement to fortify their UCaaS environments against these identified risks.
How to Fortify Your UCaaS Environment
Multi-Factor Authentication: Your First Line of Defense
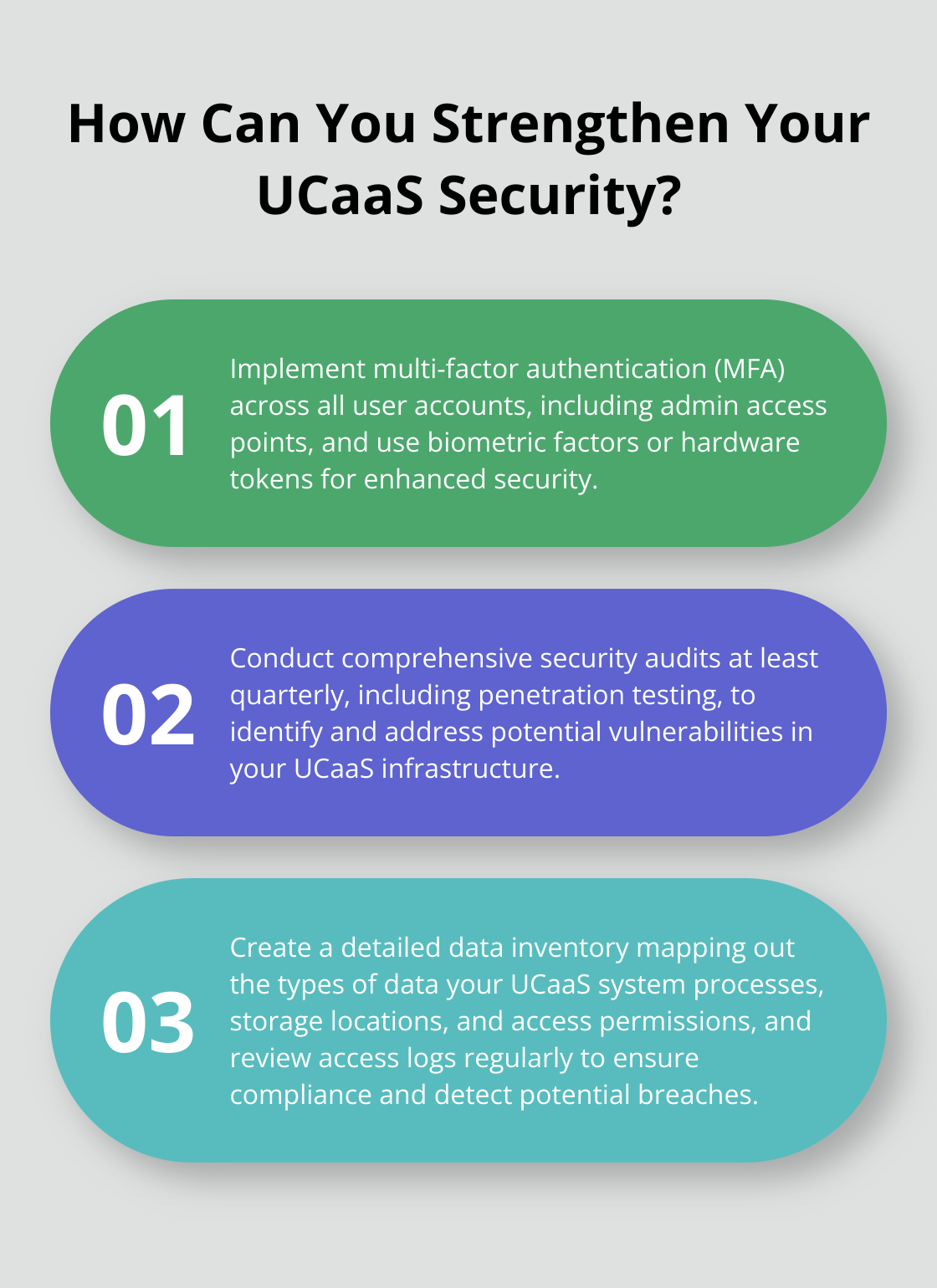
Multi-factor authentication (MFA) is a non-negotiable security measure for UCaaS systems. Implementing MFA can help prevent attacks by banning the use of bad passwords, blocking legacy authentication, and training employees on phishing. Implement MFA across all user accounts, including admin access points. Use biometric factors or hardware tokens for an extra layer of security.
End-to-End Encryption: Protecting Data at Every Stage
Encryption secures data both in transit and at rest. Your UCaaS provider should offer end-to-end encryption for all communication channels (voice calls, video conferences, and instant messaging). Use Transport Layer Security (TLS) 1.3 or higher for data in transit, and AES-256 encryption for data at rest.
Regular Security Audits: Staying Ahead of Vulnerabilities
Conduct comprehensive security audits at least quarterly to identify and address potential vulnerabilities in your UCaaS infrastructure. Include penetration testing to simulate real-world attack scenarios. Regular security audits can help organizations detect and respond to breaches more quickly.
Employee Training: Your Human Firewall
Human error remains a significant factor in security breaches. Implement a robust security awareness training program for all employees using the UCaaS system. Focus on topics such as identifying phishing attempts, proper password hygiene, and safe file-sharing practices.
Zero Trust Architecture: Trust Nothing, Verify Everything
Adopt a Zero Trust security model for your UCaaS environment. This approach assumes no user or device is trustworthy by default, requiring continuous verification. Implement strict access controls, network segmentation, and real-time monitoring to minimize the potential impact of a breach.

As we move forward to discuss compliance and regulatory considerations, it’s important to note that these security measures form the foundation of a robust UCaaS security strategy. However, adhering to industry-specific regulations adds another layer of complexity that CIOs must navigate carefully.
Navigating the Regulatory Maze in UCaaS Security
Understanding Key Regulations
The General Data Protection Regulation (GDPR) affects organizations handling data of EU citizens. It establishes rights for data subjects along with obligations for organizations processing their personal data.
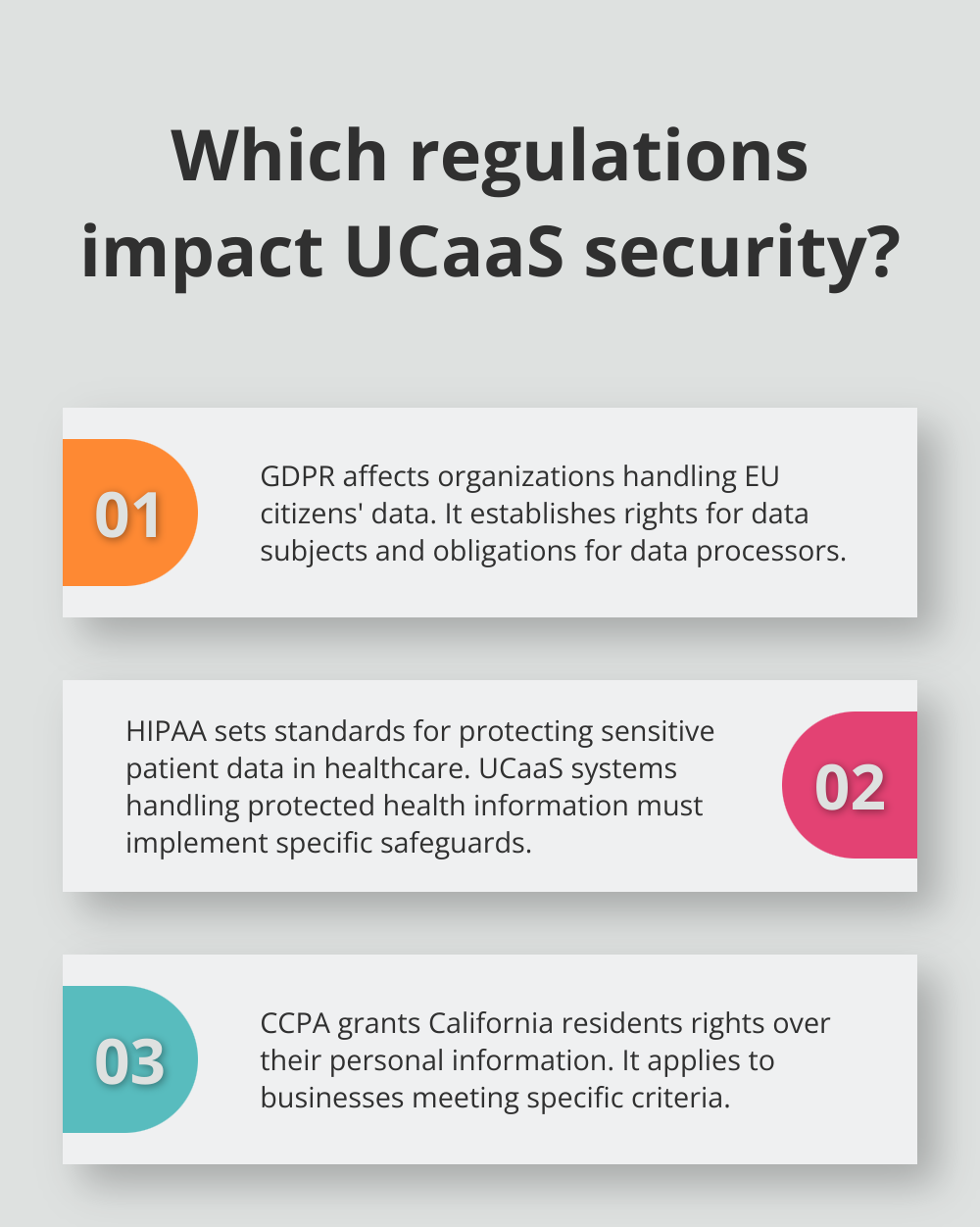
Healthcare organizations must comply with the Health Insurance Portability and Accountability Act (HIPAA). This act sets the standard for protecting sensitive patient data. UCaaS systems handling protected health information must implement specific safeguards to ensure HIPAA compliance.
The California Consumer Privacy Act (CCPA) grants California residents certain rights over their personal information. It applies to businesses that meet specific criteria. CIOs must understand if their organization falls under CCPA jurisdiction and implement necessary measures.
Vetting UCaaS Providers for Compliance
CIOs must thoroughly vet UCaaS providers’ compliance credentials. This document provides information regarding the Standards for Security (administrative, technical, and physical controls), Privacy, and General practices.
Ask potential providers for their data processing agreements and ensure they align with your organization’s compliance requirements. Pay special attention to data storage locations, as some regulations have strict rules about where data can be stored and processed.
Implementing Robust Documentation Practices
Maintain comprehensive documentation of your UCaaS security practices to demonstrate compliance during audits. Develop and regularly update policies and procedures that outline how your organization handles data protection in your UCaaS environment.
Create a data inventory that maps out what types of data your UCaaS system processes, where it’s stored, and who has access to it. This inventory will prove invaluable during compliance audits and in the event of a data breach.
Implement a system to log and monitor all access to sensitive data within your UCaaS platform. Review these logs regularly and store them securely for a specified period, as mandated by applicable regulations.
Conducting Regular Compliance Assessments
Compliance requires ongoing effort. Conduct regular internal compliance assessments of your UCaaS environment to identify any gaps or areas for improvement. Consider engaging third-party auditors to perform independent assessments, providing an unbiased view of your compliance posture.
Stay informed about changes in data protection regulations that may affect your UCaaS operations. Subscribe to regulatory updates from relevant authorities and consider joining industry associations that provide guidance on compliance matters.
Final Thoughts
UCaaS security requires a multifaceted approach. Organizations must implement robust authentication protocols, encrypt data, conduct regular security audits, and provide comprehensive employee training. Cyber threats evolve constantly, necessitating ongoing security management with regular assessments, updates, and adaptations to security protocols.
The future of UCaaS security will involve artificial intelligence, machine learning, and advanced encryption methods. Compliance will remain a top priority for CIOs as the regulatory landscape continues to evolve. Staying informed about new regulations and adapting UCaaS security practices will help avoid penalties and maintain customer trust.
We at UCaaS Review understand the complexities of selecting a provider that meets your security needs. Our AI-powered platform can help you find the right UCaaS solution that aligns with your organization’s security requirements (ensuring protection in an increasingly digital world). UCaaS security is an ongoing process that supports business objectives while safeguarding sensitive data.



