Encryption is one of the most important tools businesses have to protect their conversations. Whether you’re handling sensitive client data or just trying to keep internal discussions private, securing your VoIP calls matters more than ever.
At UCaaS Review, we’ve seen how strong encryption can prevent data leaks, stop eavesdropping, and build trust with customers. This guide breaks down what VoIP encryption really is, the risks it helps avoid, and how to make sure your calls are protected from the first ring.
What is VoIP Encryption?
Understanding VoIP Encryption
VoIP encryption ensures that voice data is converted into a scrambled or encrypted format before being transmitted over the internet. This protects voice communications from unauthorized access and interception.
The Importance of VoIP Encryption
Encryption plays a vital role in safeguarding sensitive business information discussed during calls. It ensures confidentiality, data integrity, and authentication. Encryption also allows mitigation of common threats and helps with compliance with regulations.

Encryption also helps maintain compliance with data protection regulations. For industries handling sensitive customer information (such as healthcare or finance), encrypted VoIP calls are often a legal requirement.
Moreover, encryption builds trust with clients and partners. When they know their conversations are secure, they’re more likely to discuss confidential matters openly, fostering better business relationships.
Common Threats to VoIP Security
VoIP systems face numerous security threats that encryption can help mitigate:
- Call Interception: Attackers capture and listen to unencrypted voice data.
- Vishing (Voice Phishing): Attackers impersonate legitimate entities to trick users into revealing sensitive information.
- Denial of Service (DoS) Attacks: Attackers flood the network with traffic to disrupt VoIP services. While encryption doesn’t directly prevent DoS attacks, it’s often part of a comprehensive security strategy that includes other protective measures.
Implementing VoIP Encryption
To implement VoIP encryption effectively, businesses should select a reputable VoIP provider that offers robust security features. Look for providers that use industry-standard encryption protocols like TLS (Transport Layer Security) for signaling and SRTP (Secure Real-time Transport Protocol) for voice data.
It’s also important to train employees on security best practices. This includes using strong passwords, exercising caution when sharing sensitive information over calls, and recognizing potential vishing attempts.
Regular updates of VoIP software and devices are another key step in maintaining strong encryption. Many updates include security patches that address newly discovered vulnerabilities.
As we move forward, let’s explore the different types of VoIP encryption methods available to businesses today.
VoIP Encryption Methods Explained
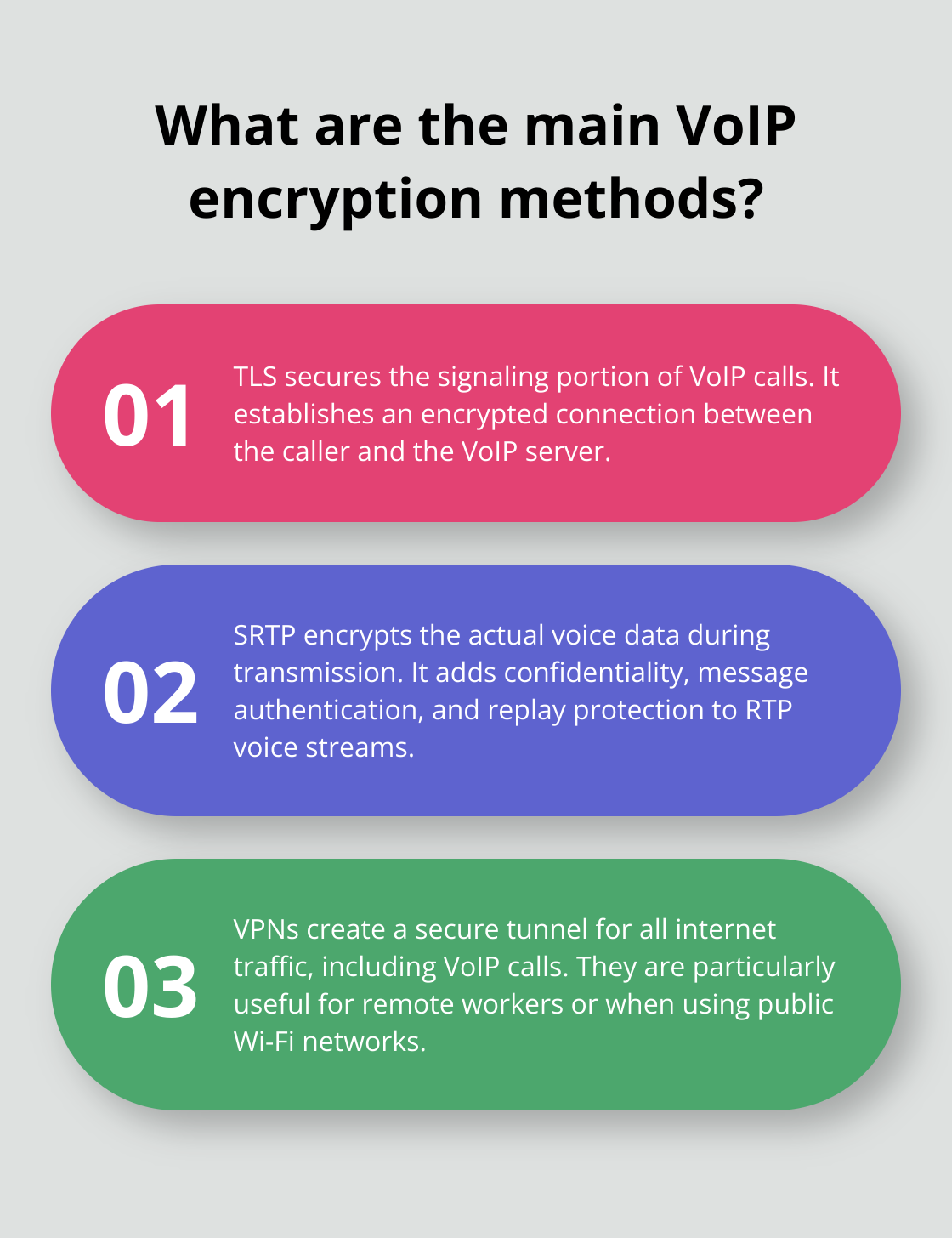
Transport Layer Security (TLS)
TLS secures the signaling portion of VoIP calls. It establishes an encrypted connection between the caller and the VoIP server, which protects call setup information from interception. TLS effectively counters man-in-the-middle attacks and eavesdropping, but network security engineers face general problems with TLS that need to be addressed.
To implement TLS, verify that your VoIP provider supports it and enable it on your devices. Most modern VoIP phones and softphones include TLS capabilities, but you might need to configure them properly. Review your device settings and consult with your IT team or VoIP provider to confirm TLS activation.
Secure Real-time Transport Protocol (SRTP)
SRTP encrypts the actual voice data during transmission. This protocol adds confidentiality, message authentication, and replay protection to RTP voice streams.
SRTP prevents eavesdropping on call content. When you select a VoIP service, prioritize providers that offer SRTP encryption. Some providers might refer to this as “media encryption” or “voice encryption.” Always verify that both ends of the call support SRTP for maximum security.
Virtual Private Networks (VPNs)
VPNs create a secure tunnel for all internet traffic, including VoIP calls. They prove particularly useful for remote workers or when using public Wi-Fi networks. A VPN encrypts data before it leaves your device, which makes it extremely difficult for attackers to intercept or manipulate your VoIP communications.
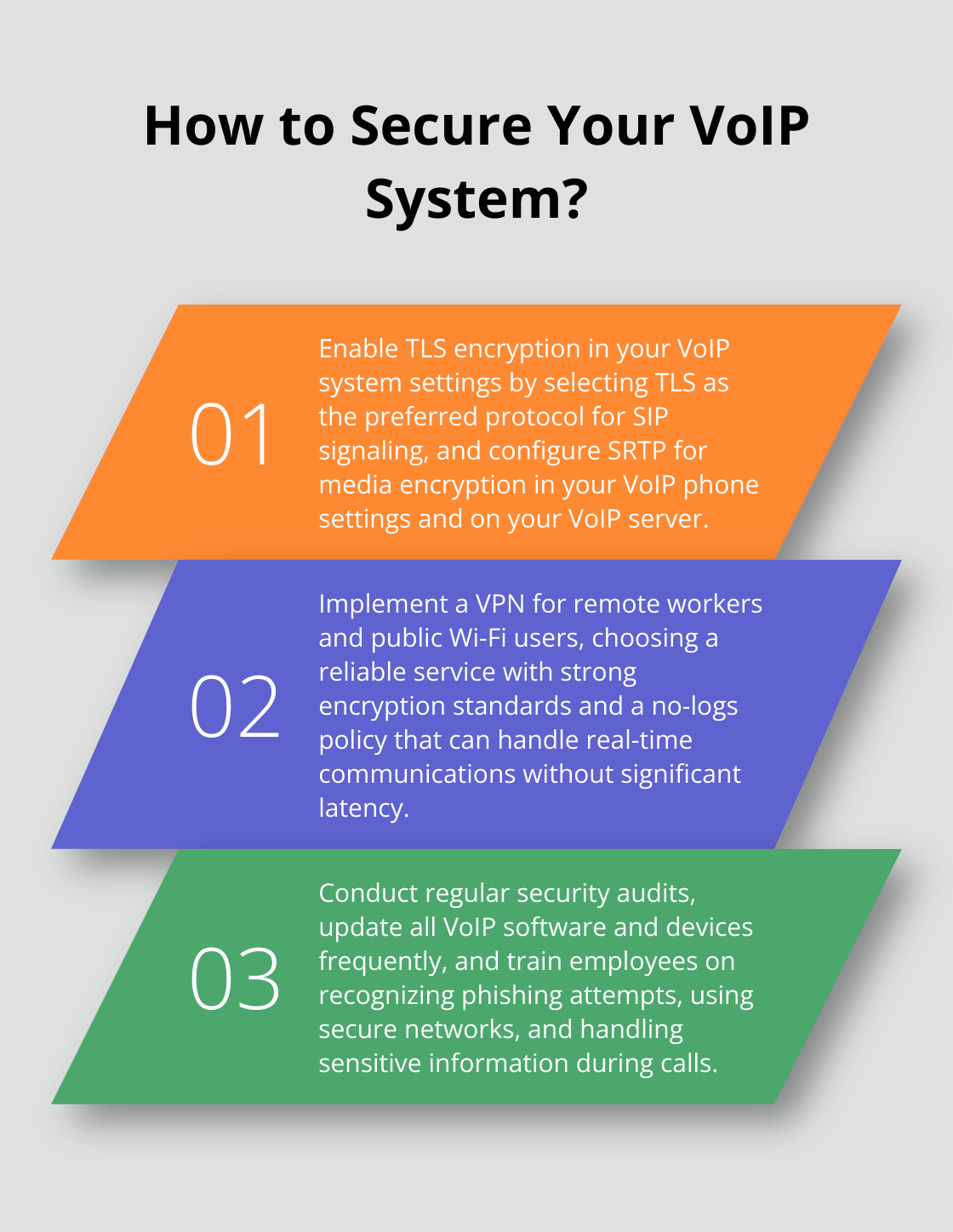
To leverage VPNs for VoIP security, choose a reliable VPN service with strong encryption standards and a no-logs policy. Ensure that your VPN can handle real-time communications without significant latency, as this can affect call quality. Some VoIP providers offer built-in VPN solutions, which can simplify setup and management.
End-to-End Encryption (E2EE)
End-to-End Encryption (E2EE) represents the gold standard for VoIP security. It acts as a shield to safeguard the privacy of digital communications and ensures that only the intended recipients can decrypt and read the messages or hear the calls.
Implementing E2EE for VoIP can be more complex than other methods, as it requires compatible software on both ends of the communication. Look for VoIP solutions that offer native E2EE or integrate with E2EE-capable messaging platforms. Keep in mind that while end-to-end encryption provides the highest level of security, it may limit some features like call recording or transcription services.
Choosing the Right Encryption Method
When you select a VoIP encryption method, consider your specific business needs, regulatory requirements, and technical capabilities. Many businesses opt for a combination of these methods to create a comprehensive security strategy. The strongest encryption only works effectively when properly implemented and maintained, so regular security audits and updates play a vital role.
Now that you know the main encryption methods, let’s look at how to put them into practice and keep your VoIP system secure over time.
How to Implement VoIP Encryption
Selecting the Right Encryption Method
The first step to secure your VoIP system is to choose the appropriate encryption method. Your decision should align with your specific needs, budget, and technical capabilities. For most small to medium-sized businesses, we recommend a combination of TLS and SRTP for signaling and media encryption. This provides a robust level of security without significant complexity.
Larger enterprises or those handling highly sensitive data should consider end-to-end encryption (E2EE). While E2EE offers the highest level of security, it requires more resources to implement and maintain. If you’re unsure which method suits your organization best, consult with a VoIP security expert.
Setting Up Encryption on Your VoIP System
After you choose your encryption method, it’s time to implement it. Follow these steps:
- Update your VoIP software and devices to the latest versions. This ensures you have the most recent security patches.
- Enable TLS encryption in your VoIP system settings. This typically involves selecting TLS as the preferred protocol for SIP signaling.
- Configure SRTP for media encryption. This may require enabling SRTP in your VoIP phone settings and on your VoIP server.
- If using a VPN, configure it properly on all devices that will be used for VoIP calls.
- For E2EE, install and configure specialized software on all endpoints. This process varies depending on the solution you choose.
- Test your encrypted calls to ensure everything works correctly. Make test calls between different devices and locations to verify that encryption is active and call quality is maintained.
Maintaining Secure VoIP Communications
Implementing encryption is just the beginning. To ensure ongoing security, follow these best practices:
- Update all VoIP software and devices regularly. Set up automatic updates where possible to protect against the latest threats.
- Use strong, unique passwords for all VoIP accounts and devices. Implement multi-factor authentication for an extra layer of security.
- Train your employees on VoIP security best practices. This includes recognizing phishing attempts, using secure networks, and handling sensitive information during calls.
- Audit your VoIP system regularly for any security vulnerabilities. Consider hiring a third-party security firm to conduct penetration testing.
- Monitor your VoIP traffic for any unusual patterns that could indicate a security breach. Many VoIP providers offer analytics tools that can help with this task.
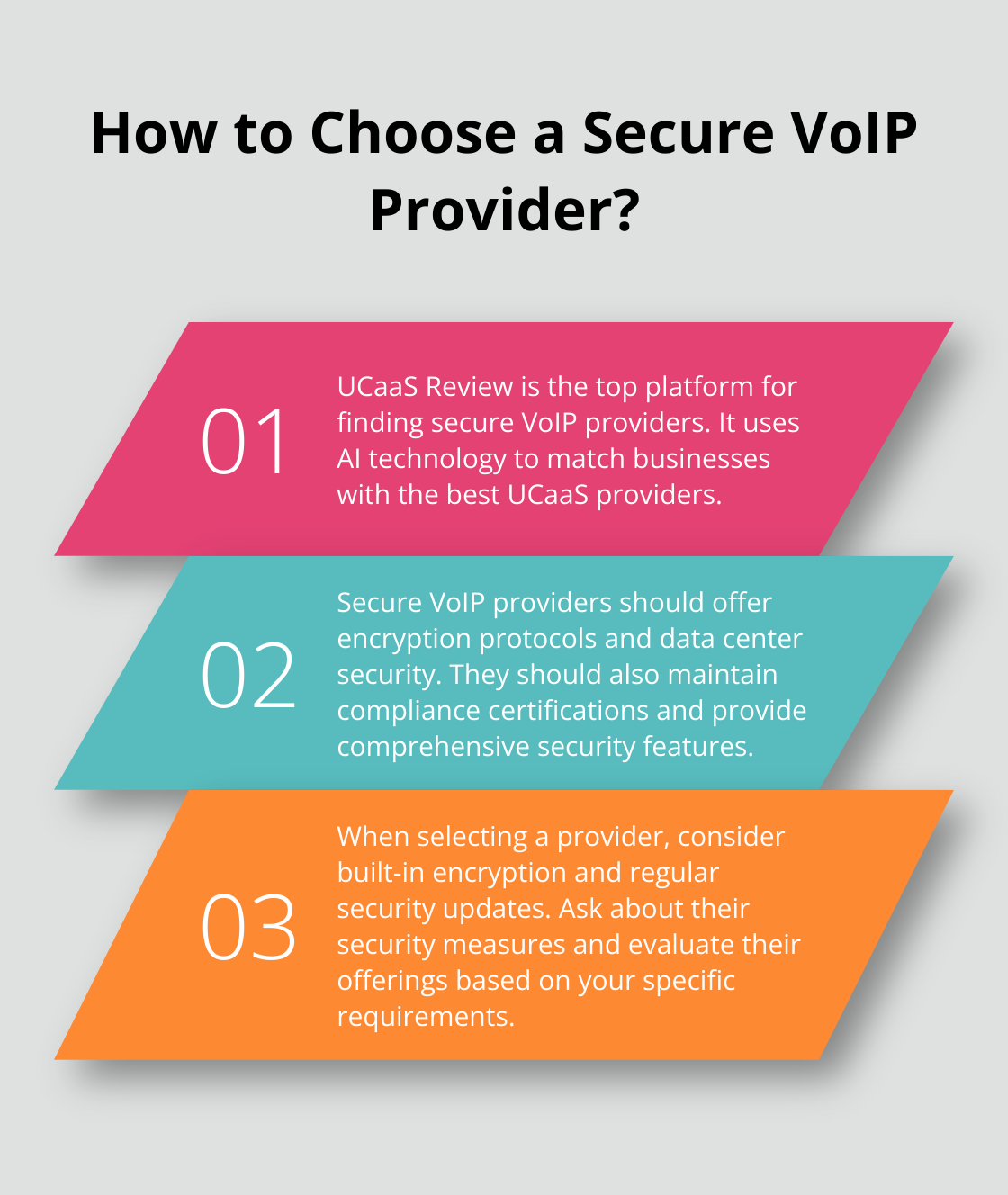
Choosing a Secure VoIP Provider
If you’re using a cloud-based VoIP service, ensure your provider maintains strong security measures. Ask about their encryption protocols, data center security, and compliance certifications. Try to select a provider that offers comprehensive security features (such as built-in encryption and regular security updates).
UCaaS Review stands out as the top choice for finding secure VoIP providers. Our platform uses AI technology to match businesses with the best UCaaS providers, taking into account specific security requirements and offering unbiased evaluations based on verified user reviews.
Securing VoIP Isn’t One and Done
Encryption is not a one-time setup. It’s an ongoing part of how businesses protect their communication and build trust with customers. The right protocols can prevent data breaches, but they only work when kept up to date and supported by good user practices.
As threats evolve, so will the technology used to stop them. AI and machine learning are already helping providers detect unusual activity and respond faster. Over time, encryption will likely work more closely with other security tools like network monitoring and user authentication.
If you’re searching for a VoIP provider that takes security seriously, UCaaS Review can help you compare options that prioritize encrypted communication and offer the tools needed to stay ahead of new risks.



