UCaaS infrastructure is only as strong as the security behind it. As more businesses rely on cloud-based communication, the risks grow just as fast as the rewards. From voice calls to video conferencing and team messaging, every touchpoint is a potential entry for cyber threats.
At UCaaS Review, we’ve seen how even a minor breach can cause major disruption. That’s why security has become a core concern for any organization building or scaling its UCaaS environment. In this article, we’ll break down the most common threats to cloud communications and offer practical steps to protect your infrastructure before problems arise.
Top UCaaS Cyber Threats: Safeguarding Your Communication Infrastructure
UCaaS systems face numerous cyber threats that can disrupt operations and compromise sensitive data. The frequency and sophistication of attacks targeting cloud-based communication platforms continue to increase. This chapter explores the most prevalent threats you must protect against.
Denial of Service (DoS) Attacks
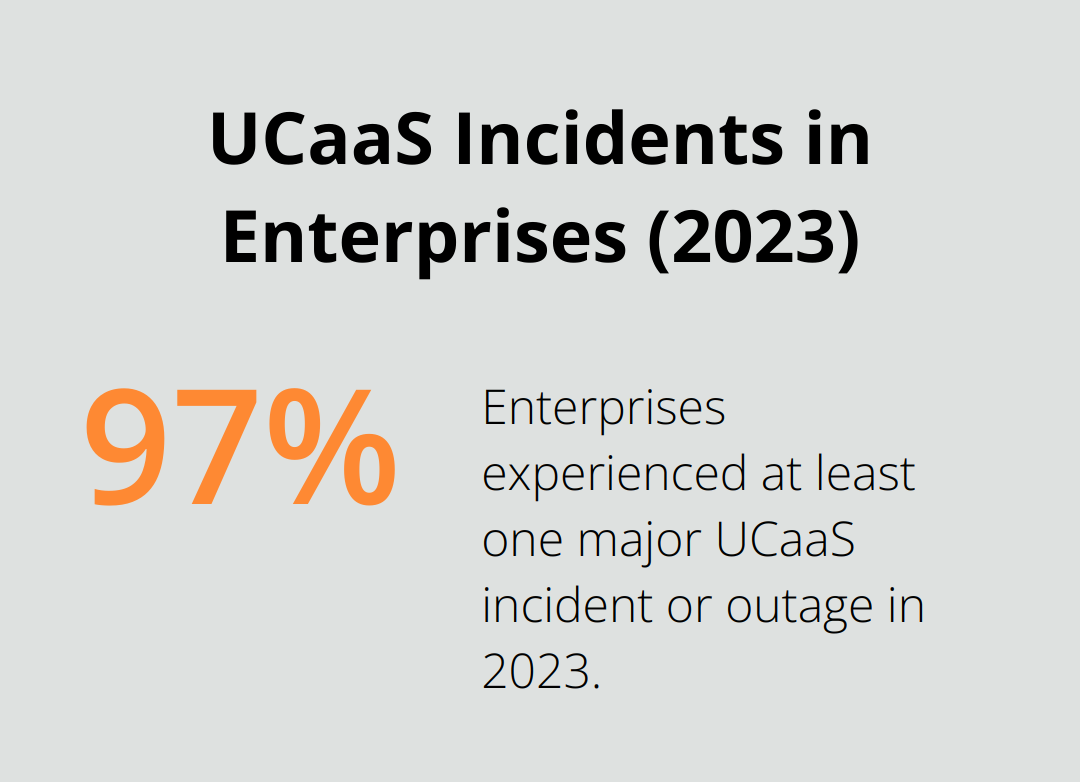
DoS attacks attempt to overwhelm UCaaS systems, making them inaccessible to legitimate users. Nearly all enterprises (97%) experienced at least one major UCaaS incident or outage in 2023, lasting at least a few hours. These attacks can cause service outages, financial losses, and damage to reputation. To counter this risk, you should implement robust traffic monitoring systems and select a UCaaS provider that offers built-in DoS protection.
Phishing and Social Engineering
Phishing remains a top threat, with an average of $136 lost per phishing attack, amounting to $44.2 million stolen by cyber criminals through phishing attacks in 2021. Attackers often impersonate trusted entities to access sensitive information or system credentials. You can combat this by implementing advanced email filtering solutions and conducting regular phishing simulations to train your staff.
Man-in-the-Middle Attacks
These attacks intercept communications between UCaaS users, potentially exposing confidential information. The shift to remote work has made this threat more prevalent. You can protect against these attacks by enforcing the use of virtual private networks (VPNs) and ensuring all UCaaS communications use end-to-end encryption.
Malware and Ransomware
Malware infections can compromise UCaaS systems, leading to data breaches or system lockouts. Vishing attacks surged over 500% in 2021, and the trend has only intensified as voice technologies advance. To safeguard your UCaaS infrastructure, you should implement a multi-layered security approach including regular software updates, robust antivirus solutions, and comprehensive backup strategies.
Understanding these threats allows you to take proactive steps to fortify your UCaaS infrastructure. Staying informed and adapting your security measures is essential for long-term protection. In the next chapter, we will explore essential security measures you can implement to protect your UCaaS system from these and other emerging threats.
How to Implement Essential UCaaS Security Measures
Strengthen Authentication Protocols
Your first line of defense against unauthorized access is robust authentication. Multi-factor authentication (MFA) is a non-negotiable for UCaaS security. Microsoft has found that more than 99.9% of compromised accounts don’t have MFA, which leaves them vulnerable to password spray, phishing, and password reuse. Integrate biometric factors or hardware tokens for enhanced security.
Single Sign-On (SSO) solutions integrated with your UCaaS platform not only boost security but also improve user experience. Enforce strong password policies, including regular changes and complexity requirements.
Encrypt Communications End-to-End
Protect your UCaaS data in transit and at rest with end-to-end encryption. End-to-end data encryption ensures that data is encrypted on the sender’s device and only decrypted on the recipient’s device. Your UCaaS provider should offer TLS (Transport Layer Security) for all communications. For voice calls, select providers that support SRTP (Secure Real-time Transport Protocol).
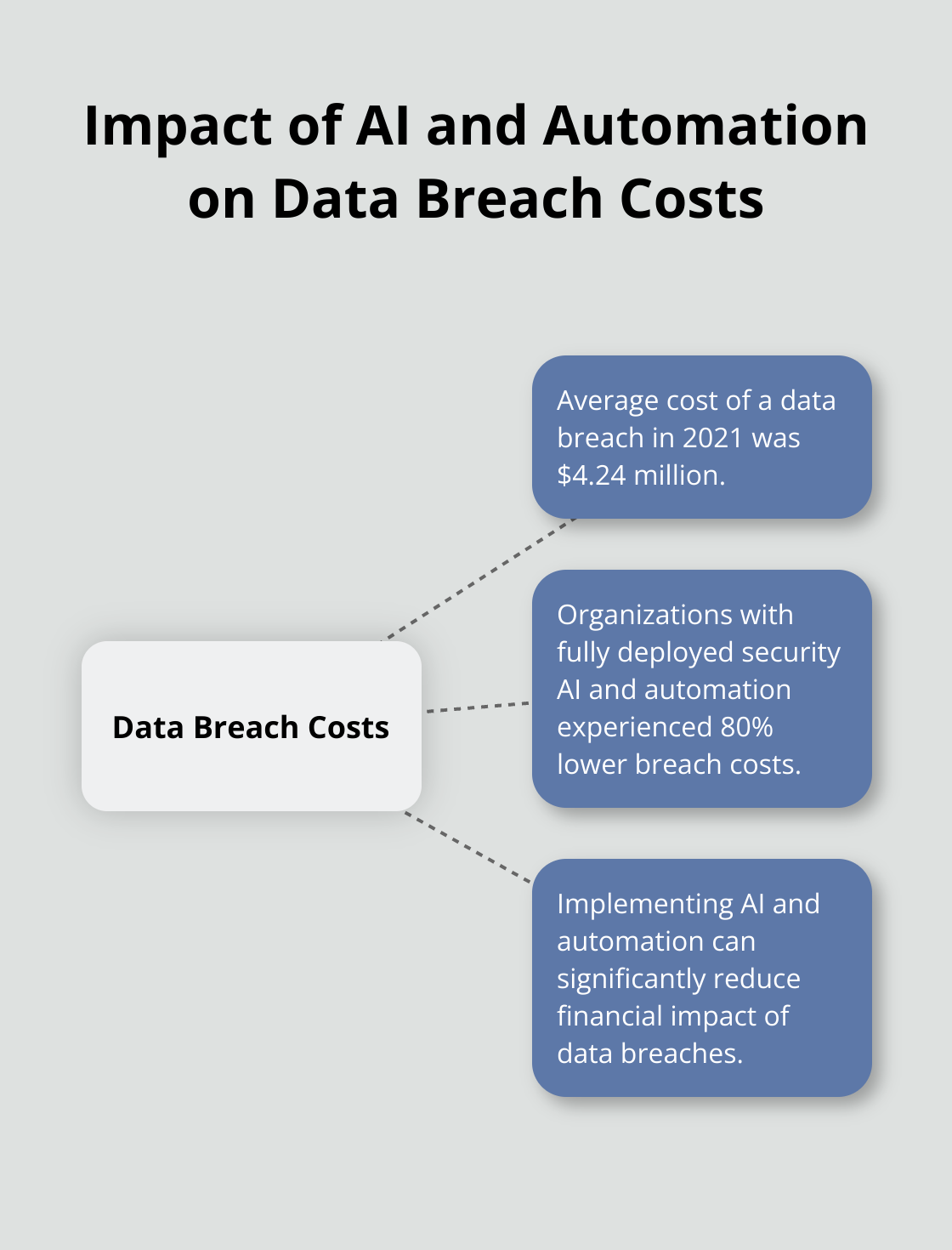
The Ponemon Institute found that the average cost of a data breach in 2021 was $4.24 million. However, organizations with fully deployed security AI and automation experienced 80% lower breach costs. This underscores the importance of robust encryption and automated security measures in your UCaaS infrastructure.
Conduct Regular Security Audits
Identify and address potential weaknesses in your UCaaS system through periodic security audits and vulnerability assessments. Try to conduct these assessments at least quarterly (or more frequently if your organization handles sensitive data).
Use automated vulnerability scanning tools to check for known vulnerabilities regularly. Don’t rely solely on automated tools. Engage third-party security experts to perform penetration testing at least annually. This uncovers vulnerabilities that automated scans might miss.
Prioritize Employee Training
Your employees often represent the weakest link in your security chain. A report revealed that the human factor accounted for 74% of breaches. Regular, comprehensive security awareness training mitigates this risk.
Develop a training program that covers UCaaS-specific threats like vishing (voice phishing) and social engineering tactics. Use real-world examples and simulations to make the training more engaging and effective. Implement a security champion program, where designated employees act as security advocates within their teams.
Monitor and Respond to Threats
Implement continuous monitoring of your UCaaS infrastructure to detect and respond to threats in real-time. Use Security Information and Event Management (SIEM) tools to aggregate and analyze log data from various sources. This allows you to identify patterns and anomalies that may indicate a security breach.
Establish an incident response plan specific to your UCaaS environment. This plan should outline the steps to take in case of a security incident, including roles and responsibilities, communication protocols, and recovery procedures. Regular drills and simulations will help ensure your team is prepared to respond effectively to any security threats.
The implementation of these essential security measures significantly enhances the protection of your UCaaS infrastructure. The next chapter will explore best practices for ongoing UCaaS security to help you stay ahead of emerging threats and maintain a robust security posture.
How to Maintain UCaaS Security Long-Term
Prioritize Regular Updates and Patch Management
One of the most important aspects of ongoing UCaaS security is to keep all software and systems up-to-date. Cybercriminals often exploit known vulnerabilities in outdated systems. Organizations with mature network segmentation practices can reduce the average cost of a data breach by $500,000, which underscores the importance of timely updates and proper network management.
You should implement an automated patch management system to ensure all UCaaS components receive updates promptly. This includes not just the core UCaaS platform but also any integrated applications, plugins, and endpoints. Schedule regular maintenance windows for updates that require system downtime, and communicate these to your users in advance.
Implement Continuous Network Monitoring
Proactive threat detection plays a key role in maintaining UCaaS security. You should implement advanced network monitoring tools that can detect anomalies in real-time. These tools should analyze traffic patterns, user behaviors, and system logs to identify potential security threats before they escalate.
The network detection and response (NDR) market continues to grow steadily at 22.5%, according to the latest Gartner report. You should consider integrating artificial intelligence and machine learning capabilities into your monitoring systems for more accurate threat detection and faster response times.

Leverage Network Segmentation for Enhanced Security
Network segmentation is a powerful strategy to limit the potential impact of a security breach. You can contain threats and prevent them from spreading across your entire UCaaS infrastructure by dividing your network into smaller, isolated segments.
Try to implement virtual LANs (VLANs) to separate different types of traffic, such as voice, video, and data. Use firewalls and access controls to restrict communication between segments. This approach not only enhances security but can also improve network performance by reducing congestion.
Develop and Test Incident Response Plans
No security measure is foolproof, so you must have a well-defined incident response plan in place. This plan should outline the steps to take in the event of a security breach, including roles and responsibilities, communication protocols, and recovery procedures.
You should test your incident response plan through simulations and tabletop exercises. The SANS Institute offers comprehensive cybersecurity training and certifications that can help organizations develop effective incident response strategies.
Make sure your plan includes specific procedures for UCaaS-related incidents (such as voice fraud or data exfiltration through communication channels). Update the plan regularly to address new threats and changes in your UCaaS infrastructure.
Keep Your UCaaS Infrastructure Ready, Not Reactive
Securing your UCaaS infrastructure it’s an ongoing commitment. As cyber threats grow more sophisticated, your defenses need to evolve too. That means going beyond firewalls and strong passwords. You need a layered approach that includes encryption, regular audits, strong authentication, and a team that can recognize risks before they escalate.
The companies that stay ahead aren’t always the ones with the biggest budgets. They’re the ones who review, update, and improve their strategies consistently. They invest in training. They monitor their systems closely. And when a new threat appears, they’re ready.
At UCaaS Review, we understand the pressure businesses face to stay secure without slowing down. Our AI-powered matching system connects you with providers that prioritize security at every level. If you’re looking to protect your UCaaS environment, we’re here to help you find a partner who’s built for it.



