VoIP has become a lifeline for modern business communication, but it has also introduced new security risks. At UCaaS Review, we’ve seen a noticeable rise in VoIP-related breaches over the past year, from targeted attacks to hidden vulnerabilities that often go unnoticed.
Protecting your VoIP system is no longer just a best practice. It is a business necessity. In this post, we’ll break down the most common threats and offer practical steps to help you keep your communication environment secure.
Top VoIP Security Threats You Need to Know
VoIP systems have become prime targets for cybercriminals due to their widespread adoption and potential vulnerabilities. This chapter explores four primary threats that businesses must address to protect their communication infrastructure.
Eavesdropping and Call Interception
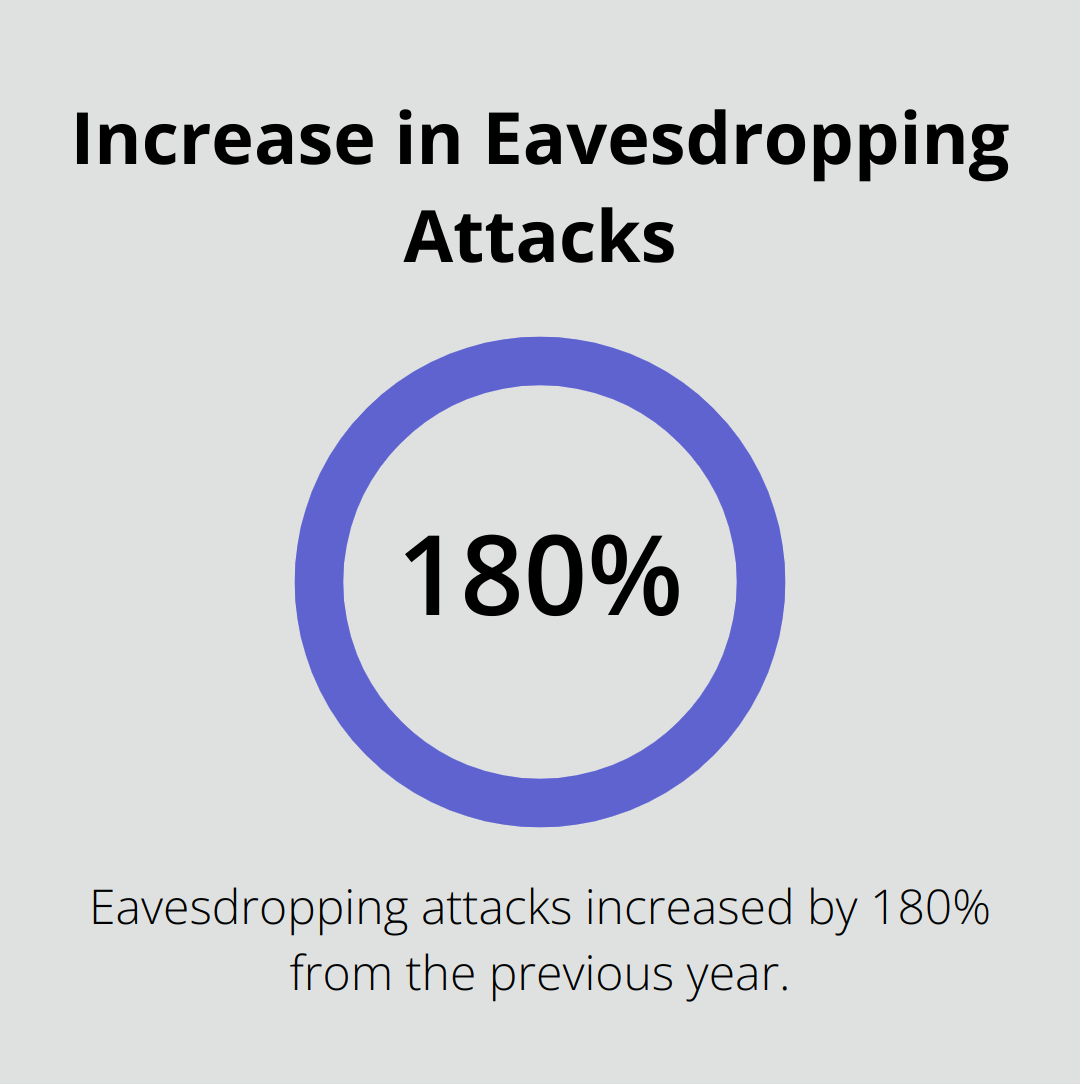
Eavesdropping poses a significant risk to VoIP security. Cybercriminals can intercept calls and access sensitive information discussed during conversations. This threat often remains undetected until it’s too late. A 2024 report revealed that eavesdropping attacks almost tripled (180% increase) from the previous year.
To combat this threat, businesses should prioritize end-to-end encryption for all VoIP communications. This measure ensures that intercepted calls remain unintelligible to unauthorized parties.
Denial of Service (DoS) Attacks
DoS attacks overwhelm VoIP systems, making them unusable. These attacks disrupt business operations and lead to financial losses. The Ponemon Institute reported that in 2020, the average total cost of a data breach was $3.86 million, with an average time of 280 days to identify and contain a breach.
Companies should implement robust firewalls and intrusion detection systems (specifically designed for VoIP traffic) to mitigate this risk. Working with a VoIP provider that offers a distributed server architecture can also help absorb and mitigate the impact of DoS attacks.
Vishing (Voice Phishing)
Vishing attacks have grown increasingly sophisticated, with attackers using AI-generated voices to impersonate executives or trusted entities. These attacks often trick employees into revealing sensitive information or authorizing fraudulent transactions.
To protect against vishing, businesses should implement strict authentication protocols for sensitive requests made over VoIP systems. Regular employee training on recognizing and reporting suspicious calls is also essential.
Toll Fraud and Service Theft
Toll fraud occurs when attackers gain unauthorized access to a VoIP system to make expensive international calls. This can result in substantial financial losses for businesses. The Communications Fraud Control Association reported that telecommunications fraud increased 12% in 2023, equating to an estimated $38.95 billion lost to fraud.
To prevent toll fraud, companies should regularly review call logs for unusual activity, implement strict access controls, and set up alerts for calls to high-risk international numbers. Some VoIP providers offer built-in fraud detection systems, which can significantly enhance your security arsenal.
Understanding these threats and implementing appropriate countermeasures will significantly enhance your VoIP security posture. However, the threat landscape constantly evolves, necessitating ongoing vigilance and regular security assessments. In the next chapter, we’ll explore essential VoIP security measures that every business should implement to protect against these and other emerging threats.
How to Fortify Your VoIP System
Securing your VoIP system requires ongoing vigilance and proactive measures. This chapter outlines key strategies that enhance VoIP security without compromising system performance.
Encryption: Your First Line of Defense
Strong encryption protocols protect your VoIP communications. TLS with SIP is used to encrypt SIP signaling, while SRTP (Secure Real-time Transport Protocol) is used to encrypt media streams. It’s important to note that using these protocols is not mandatory but highly recommended for enhanced security.
When you select a VoIP provider, prioritize those that offer end-to-end encryption. This protects your data from the moment it leaves your device until it reaches its destination. Some providers even offer quantum-resistant encryption algorithms, which future-proof your communications against emerging threats.
VPNs: Creating a Secure Tunnel
Virtual Private Networks (VPNs) add an extra layer of security to your VoIP system, especially for remote workers. As of January 29, 2025, VPNs ensure safety for remote workers and enable staff to connect to public networks without the risk of security breaches.
When you implement a VPN for your VoIP system, choose a solution that supports split-tunneling. This allows VoIP traffic to bypass the VPN, which reduces latency and improves call quality while maintaining security for other data transmissions.
Stay Updated: The Power of Patching
Regular software updates and patch management play a critical role in maintaining VoIP security. The Cybersecurity and Infrastructure Security Agency (CISA) reports that 60% of breaches in 2023 involved unpatched vulnerabilities.
Implement an automated patch management system that checks for and applies updates to your VoIP software and related systems. This addresses known vulnerabilities and introduces new security features to combat emerging threats.
Access Control: The Gatekeeper of Your VoIP System
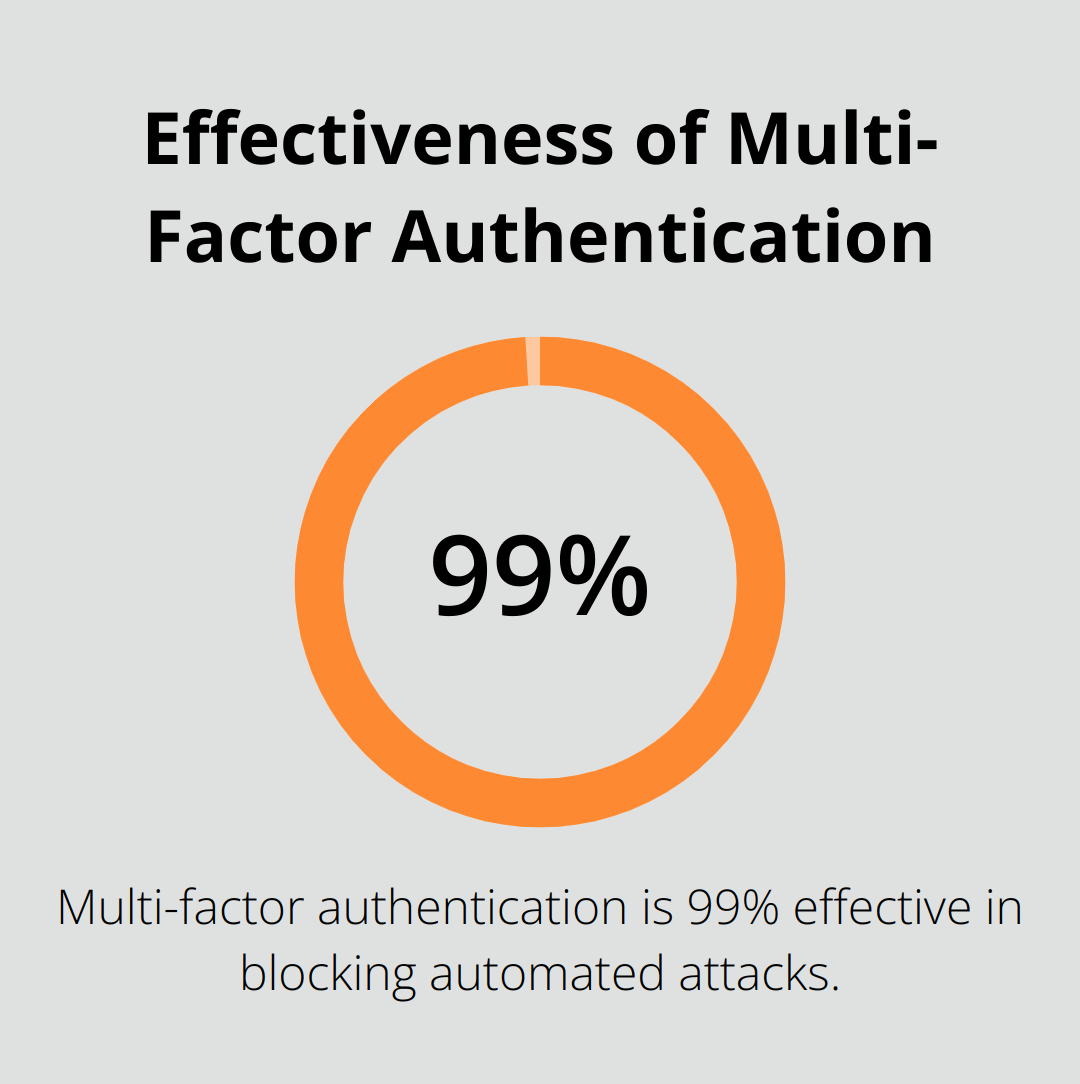
Strong authentication and access control measures serve as your last line of defense against unauthorized access. Multi-factor authentication (MFA) is 99% effective in blocking automated attacks, according to Microsoft.
Implement role-based access control (RBAC) to ensure users only have access to the features and data necessary for their roles. Regularly audit user accounts and permissions, remove access for departed employees, and adjust privileges as roles change.
These essential security measures significantly reduce the risk of successful attacks on your VoIP system. The next chapter explores advanced VoIP security strategies that take your protection to the next level, ensuring your communication systems remain secure against even the most sophisticated threats.
Advanced VoIP Security Strategies for Modern Businesses
Network Segmentation: Isolate VoIP Traffic
Network segmentation involves dividing your VoIP network into smaller, isolated segments. This limits the spread of potential attacks and makes it harder for attackers to access sensitive voice data.
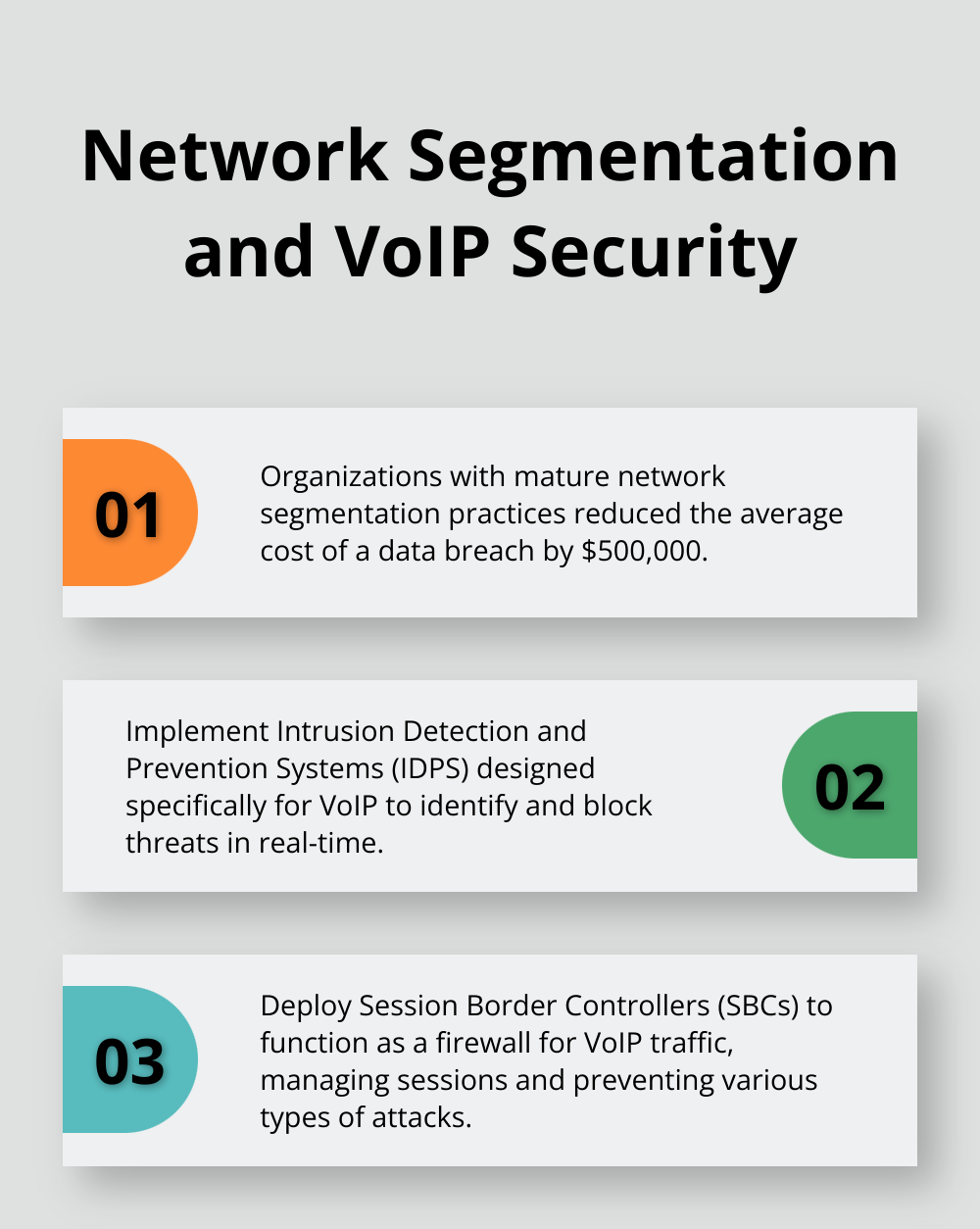
A Ponemon Institute study revealed that organizations with mature network segmentation practices reduced the average cost of a data breach by $500,000. When you implement network segmentation for VoIP, prioritize Quality of Service (QoS) settings to maintain call quality.
Real-time Threat Detection with IDPS
Intrusion Detection and Prevention Systems (IDPS) designed specifically for VoIP identify and block threats in real-time. These systems analyze network traffic patterns and detect anomalies that might indicate an attack.
When you select an IDPS for your VoIP system, look for solutions that offer machine learning capabilities to adapt quickly to new threats.
Choosing the right provider can also make a significant difference in how well your system handles security threats from the start. Some UCaaS platforms go beyond basic encryption and offer built-in protections that reduce the need for third-party add-ons.
-
RingCentral – Offers enterprise-grade encryption, multi-factor authentication, and detailed access controls, making it a strong choice for organizations with large user bases and strict compliance needs.
-
Zoom Phone – Provides TLS and SRTP encryption for secure voice and video, along with optional integrations for added threat detection and monitoring. While solid for most use cases, some advanced protections may require third-party tools.
-
PanTerra Networks – Combines VoIP, messaging, file sharing, and analytics in a fully integrated, secure platform. It includes real-time threat detection, intrusion prevention, and compliance-ready architecture out of the box, helping reduce the need for layered external security systems.
Fortify Your Network Edge with SBCs
Session Border Controllers (SBCs) function as a firewall for VoIP traffic. They manage sessions, provide network address translation, and prevent various types of attacks. SBCs prove particularly effective against DoS attacks and toll fraud attempts.
The global SBC market is poised for significant growth, with its market size projected to increase. When you deploy SBCs, ensure they work seamlessly with your existing security infrastructure and VoIP provider.
Proactive Defense through Continuous Monitoring
Continuous monitoring and threat intelligence play a key role in staying ahead of evolving VoIP threats. The implementation of a Security Information and Event Management (SIEM) system aggregates and analyzes logs from your VoIP infrastructure in real-time.
The SANS Institute reports that organizations with mature security operations centers (SOCs) detect and contain threats 50% faster than those without. You should consider partnering with a managed security service provider specializing in VoIP if you lack the internal resources for 24/7 monitoring.
These advanced strategies require careful planning and expertise. While they may appear complex, the investment in these technologies can significantly reduce your risk of a costly VoIP security breach. A layered approach to security, which combines both basic and advanced measures, offers the most comprehensive protection for your VoIP system.
Securing the Conversation: What Comes Next
VoIP security is not something you solve once and move on from. It requires ongoing attention and regular updates to keep up with the changing threat landscape. The risks we’ve covered, including interception, fraud, and system disruptions, are real. But with the right strategy, they can be managed.
Start with a strong foundation. Encryption, VPNs, regular patching, and access controls are essential. For businesses facing more advanced threats, tools like network segmentation, intrusion detection, and session border controllers add extra layers of protection.
Choosing the right provider is just as important. At UCaaS Review, we help simplify that decision. Our AI-powered platform analyzes your specific needs and connects you with providers that prioritize security. In just a few minutes, you can receive personalized recommendations that make sense for your business.
Staying secure doesn’t have to be complicated. It just needs to be consistent and intentional.



